NFC Android hack is real, but you probably won’t get a virus “beamed” to your smartphone
Earlier this week, there was quite a bit of news going around about a big NFC hack on Android and Nokia smartphones that would supposedly allow any hacker to “beam” malicious code or malware onto your device, without your knowledge. While this is in part true, the exploit isn’t quite as massive of a security flaw as some blogs would have you think. Helpfully explained by Android Central, the general idea is this: While the NFC hacks demonstrated at a Black Hat conference this week do have the potential to take over an Android device, their potential for actual use in the real world is fairly limited.
The worst case scenario was one demonstrated on a Nexus S, running the outdated Android 2.3 Gingerbread. By exploiting a flaw in Gingerbread’s memory management though a NFC tag, the hacker was able to run malicious code and take control of the device. However, there are a few factors that make this particular exploit a bit less dangerous than it seems. First off, the NFC stack flaw is found only in Gingerbread, so in order for your phone to be hacked, you must have both NFC and Gingerbread. Since the Nexus S should already have been updated to Android 4.0, there should be very few devices on the market which are actually vulnerable to this attack. Then there’s the issue of distance. Your phone’s NFC could theoretically be activated and used without your knowledge, but it would be quite difficult. For example, in my experience with NFC, the feature doesn’t work until the devices are nearly touching. It then follows that if you have your smartphone in your pocket, then anyone trying to hack it via NFC would likely have to press their device against your pocket in order for NFC to work. As such, it isn’t the most subtle of hacks.
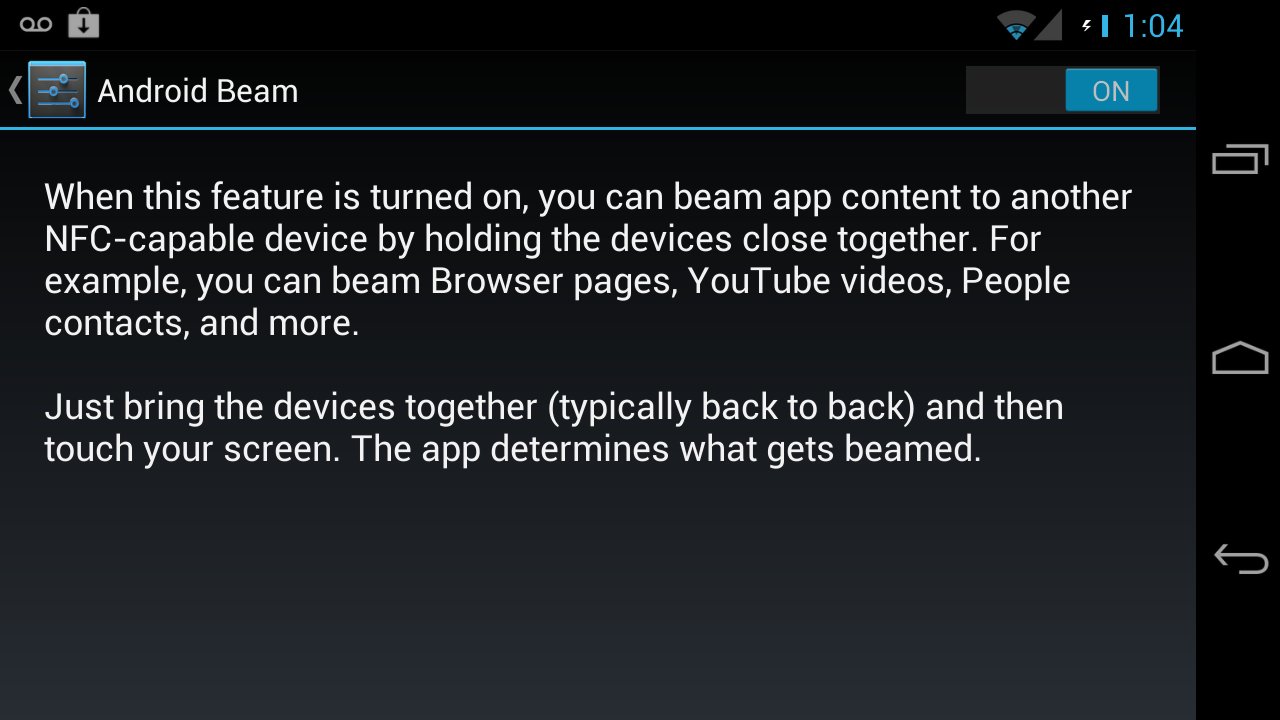
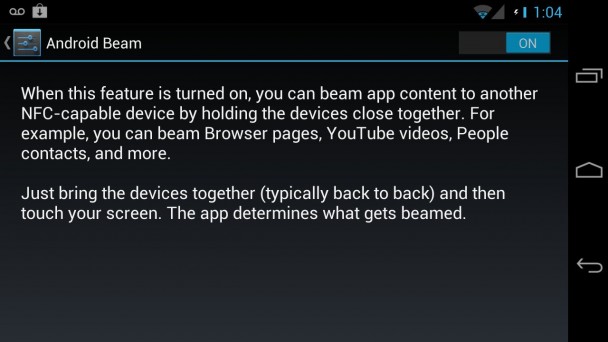
The second demonstrated hack is actually not an NFC stack exploit, but more of a security concern coupled with a browser exploit. This time using a Galaxy Nexus on Android 4.0.1, a hack was demonstrated where NFC was used to send the device to a malicious website, which exploited a browser vulnerability to gain access to the device. Of course, the same thing would happen if a hacker could get you to access the malicious site through other means like an email, which is why this hack isn’t really NFC based. Not only that, the browser vulnerability demonstrated is only present on Android 4.0.1, so a properly updated device would not be vulnerable. What the hack does do, however, is bring up a slight security concern with Android Beam. Because the user doesn’t get to choose whether or not to open a link beamed to them, NFC could potentially be used to “force” users to visit malicious sites that they didn’t intend to. This could be easily fixed by a confirmation dialogue, but that would have to be added to Android Beam.
So, while the exploits were quite impressive and do exist, they aren’t likely to be as much of a problem for users as many seem to think. The only exploit that hasn’t been patched in the latest version of Android is the automatic link opening, and in order to take advantage of that a hacker would have to find a new browser vulnerability and get close enough to activate the NFC tag. Even if you are running a version of Android with the security flaw, any hacker would still have to get a device within millimeters of your phone without you noticing them or the NFC vibration. As such, while it wouldn’t hurt for Google to add a confirmation dialogue to Beam and perhaps make NFC transfers a bit more secure, it isn’t likely that your phone will be comprised through a NFC hack any time soon.
[Ars Technica via Android Central]