Major security hole found in AOSP Android browser
The brilliant folks over at Rootz Wiki have discovered a major security hole that potentially puts a majority of rooted Android users at risk of having sensitive passwords compromised. The vulnerability only affects those who use the default Android browser to remember their passwords for the websites that they frequent.
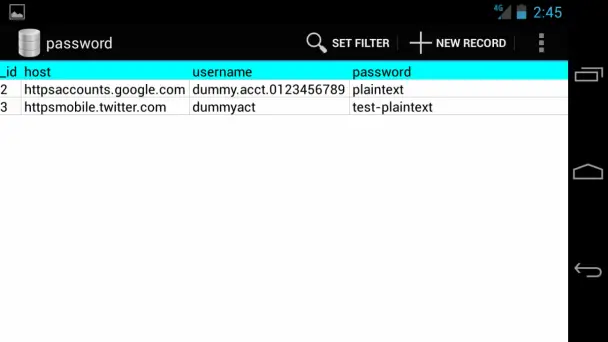
Apparently, the stock browser stores the remembered passwords in plain text in an SQL database found at /data/data/com.android.browser/databases/webview.db, in a table named password.
This does not affect the Chrome browser, which actually is the stock browser on newer Nexus devices like the ASUS Nexus 7 or the LG Nexus 4. However, older devices that run AOSP, devices with a manufacturer skin that includes the AOSP browser (or a skinned version of it), or AOSP/AOKP custom ROMs that use the AOSP browser are all potentially at risk. Rooted users are most at risk, since potentially any app that has root access could read these passwords.
AOKP developers are already hard at work on a fix, but in the meantime, our official advice would be to clear all of your browser’s data and then use an alternate browser instead (like Chrome), until a fix is available for your device – either from Google directly, your device’s manufacturer, or a your custom ROM’s developers.
[Rootz Wiki] Thanks, Paul!

