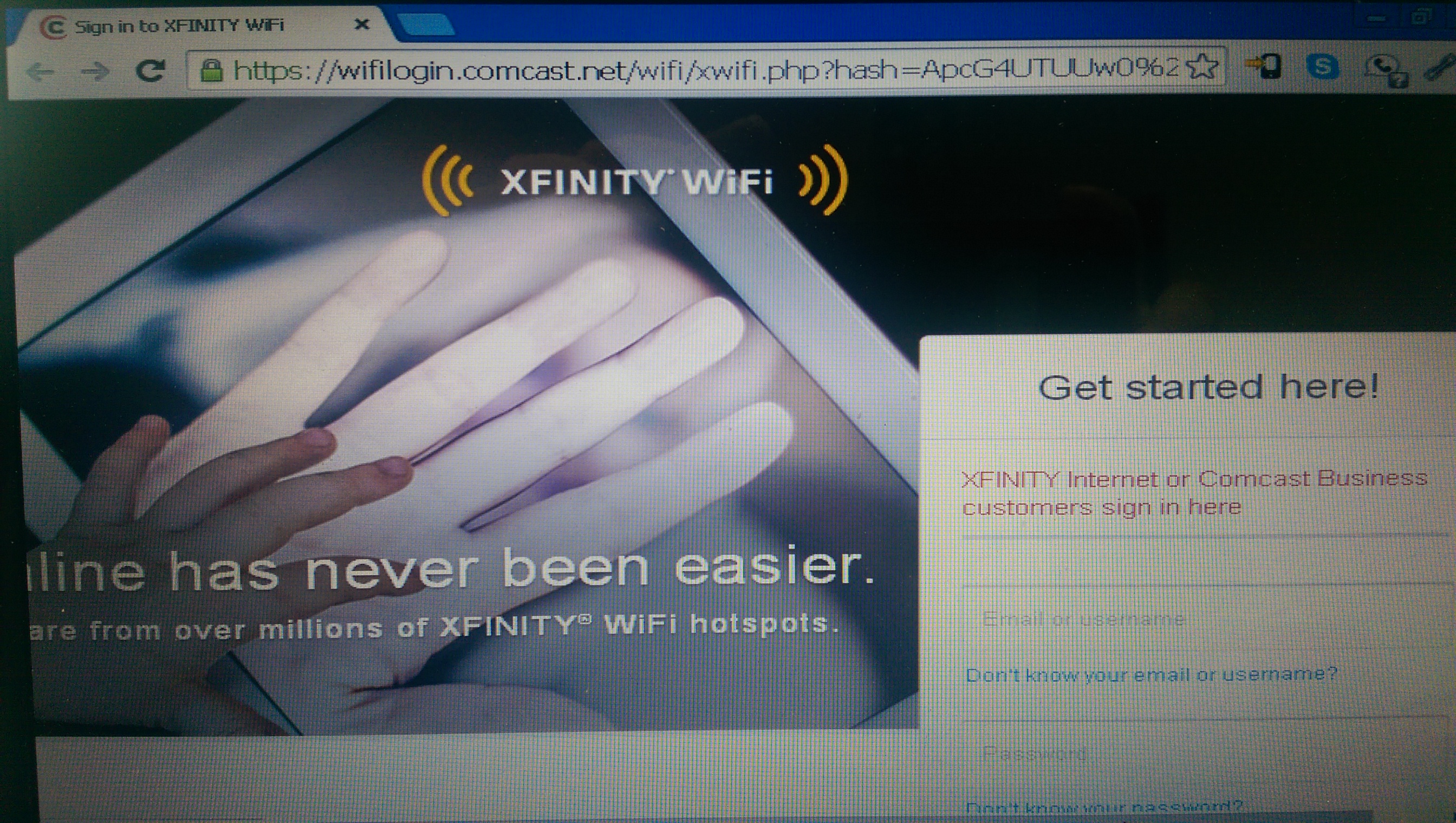
The dangers of trusted unsecured WiFi access points
 Something that I’ve been noticing more and more in my town is the prevalence of unsecured Wifi access points named “xfinitywifi.” These are unsecured access points that connect you to the Comcast/XFinity network and generally will request a password on a landing page if you don’t have a connection optimizer that presents that automatically for you. AT&T users may be more familiar with the “attwifi” hotspots.
Something that I’ve been noticing more and more in my town is the prevalence of unsecured Wifi access points named “xfinitywifi.” These are unsecured access points that connect you to the Comcast/XFinity network and generally will request a password on a landing page if you don’t have a connection optimizer that presents that automatically for you. AT&T users may be more familiar with the “attwifi” hotspots.
If you know much about internet security, you might want to skip this as it’ll probably seem laughable to you. I play with phones, not internet security as a hobby, so some of this came as news to me. It’ll probably be a “well derp,” to you.
Recently an unsecured WiFi access point popped up at the building where I work. I realized this because I was connected to it instead of my work’s network and had been transmitting work and personal info via the xfinitywifi connection.
I’d connected to an xfinitywifi connection a couple of weeks back while I was stuck in line attempting to return some Comcast equipment, and my phone had reconnected me to this access point as I’d never cleared the saved connection.
It got me to wondering what would prevent someone from impersonating this (or any) previously trusted open hotspot and grabbing my username and password or setting up for a man in the middle attack. The answer to that evidently is nothing. Nothing prevents that.
As a test I changed the WiFi hotspot name on my HTC One M8 to xfinitywifi and checked to see if my laptop would auto connect. It did. A little while later someone walked into the building I work at, connected through my hotspot, and I shut it down. I didn’t even have to DDOS or kill the router that was broadcasting the real xfinitywifi, I simply had to be closer to the people who were connecting (which my office is).
A little research on the subject and I found that Arstechnica had reported on this last month and concluded that there’s pretty much no protections when you connect automatically, you’re just opening yourself up to be hacked.
 You can take it a little further and execute attacks that render most current forms of security null, or present you fake web pages (for banks, wifi login, etc.) to grab usernames and passwords.
You can take it a little further and execute attacks that render most current forms of security null, or present you fake web pages (for banks, wifi login, etc.) to grab usernames and passwords.
It’s pretty easy to present a fake web page, grab your info and forward you to the right page if you’re the subject of a man in the middle attack. It’s significantly harder to fake SSL, but it is still possible.
My initial thought on this is that basically as long as I didn’t go to a secure site or enter a password there wasn’t much someone could steal, but using a sophisticated man in the middle attack you can probably grab login tokens for services that sync while connected. Potentially even those with recently patched OpenSSL post-Heartbleed services.
You might be able to argue that that’s not possible at the moment, however if you’re in security, give it a week. You know how these things work.
Other fun things that can be done are inject code into web pages to exploit browser problems you might have, swap out advertising, flip the net upside down, and just completely wreak havoc by intercepting what you post online and posting spam instead.
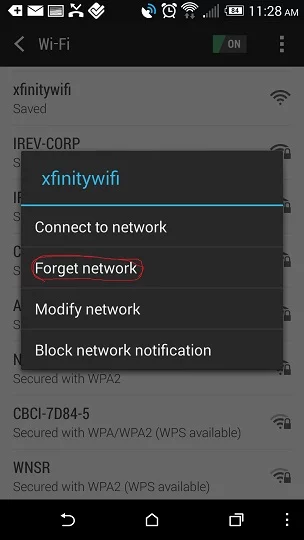
So unless you’re extremely confident that you’re connecting to the right hotspot and it’s not a cell phone acting as a WiFi hotspot that someone charged, slapped above a ceiling tile in the bathroom, and is spending the day packet sniffing or changing DNS to fake you out into giving them your password, just don’t let these connections be saved.
If you’re wondering how to un-save a network, go to settings, WiFi, long press the network, forget network.
If you’re not on your personal equipment for an internet connection, play it safe. Better slow cell data when unsure than spending weeks changing passwords, reporting stolen identity, etc.
I’m pretty sure the owners of the open WiFi hotspot networks can come up with some method to verify that you’re connected to a real one or warn you that you aren’t. That probably won’t be as easy to fake, but those apps don’t seem to be out yet and probably won’t until this becomes a widespread problem.
Play it safe and assume at all times if something seems like it could be insecure, it probably is somehow.