First malicious Xposed module reported in the wild
 A bulletin posted Friday on the SonicWALL Security Center (Dell’s security software/hardware/company,) details the emergence of the first Xposed malware.
A bulletin posted Friday on the SonicWALL Security Center (Dell’s security software/hardware/company,) details the emergence of the first Xposed malware.
Unfortunately in over one thousand words they don’t bother to tell you what the malicious module is named, but they do mention several modules that have absolutely nothing to do with the malicious one – so if you’re looking for a module name, they’ll give you several to be wary of that you don’t need to be wary of.
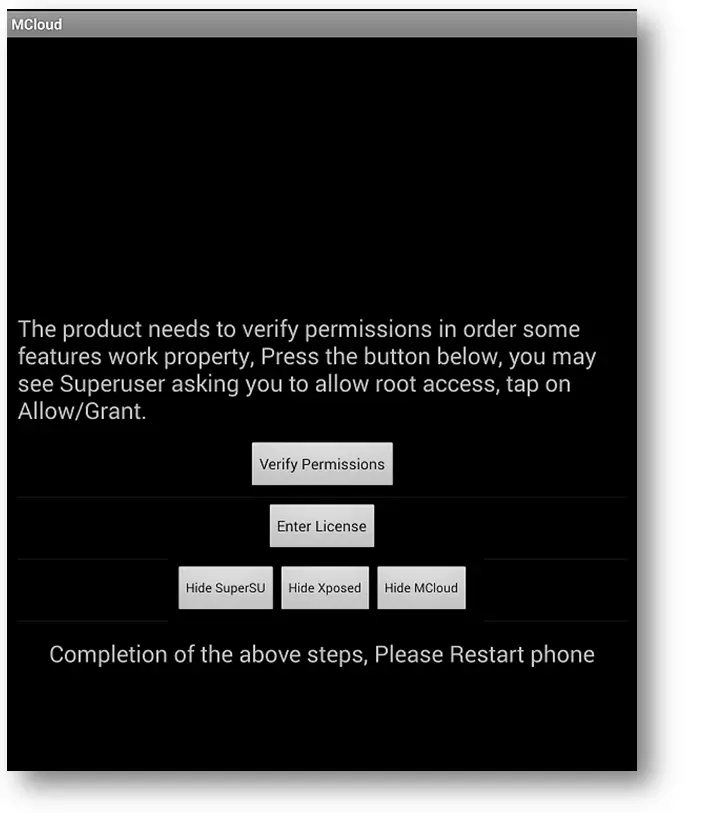
Fortunately there’s one screenshot included of the malicious app and it says “MCloud” in the top, so we’re going to go with the assumption that that is the name of the malicious module they took great pains to document but didn’t bother naming. Maybe it’s not, but it’s one of the screen shots listed alongside “Tinted Status Bar,” which I’m assuming has nothing to do with this other than to have their name dragged into the mix.
The long and short, which is beautifully detailed on the SonicALERT page, is that the malicious app steals passwords by intercepting keystrokes in password fields, has access to QQ Friends/History, WhatsApp Friends and messages, call history, album upload (I guess if they want your music?) start sound recording (so they can listen to the room,) restart the device, and a host of other things. They control your phone.
It should be noted that in order to be affected you have to have unlocked your bootloader, rooted your phone, installed a custom recovery software/superuser, installed the Xposed framework, and then have been tricked into installing the application that contains the malicious code, going to the Xposed module manager, activate the malicious Xposed module, reboot, and potentially give it superuser access as well. So if you don’t recall doing that series of actions, most likely you’re safe.
This does go to show a few things – how popular the notion of being able to mod Android on the fly has become, and that there’s absolutely no security when you disable security as you’ve had to do to get to the point you could be affected by this module.
Root is fun and all, but with root access comes root access. With Xposed everything pretty much runs with that access, although it appears this particular malware they’re documenting may have a component that requires a bit more elevated permission than usual.
I’ll also point out while this is being heralded as the first malicious Xposed module, but that is a relative term. There are several Xposed modules that actively deny developers or content producers income, that provide workarounds to security measures that were put in place for reasons, and a couple that have been removed for outright breaking copyright and code protection to steal product. This is just the first rootkit-style malicious app.
So, be wary of strange people offering you free Xposed modules and you should probably be fine.
[MySonicWall.com]