The dangers of Dev-Host
 Dev-Host is a free file sharing site aimed primarily at developers and the ROM community. Up until sometime last year, the people running it may have had some questionable advertising, but there was nothing particularly insidious. Sadly that’s changed.
Dev-Host is a free file sharing site aimed primarily at developers and the ROM community. Up until sometime last year, the people running it may have had some questionable advertising, but there was nothing particularly insidious. Sadly that’s changed.
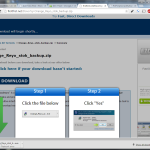
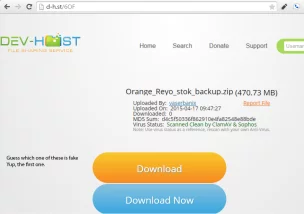
For the past two weeks (and significantly more judging by comments on my Google+ post), I’ve observed that they, or their advertisers, have popped up a fake download button that directs traffic to a malware install site.
While free hosting sites are notoriously underfunded and tend to have to make deals with the highest, and sometimes scummiest, advertising bidders they’ve actively slapped in a download button above the real one to direct you to a download page that installs a piece of malware called Multiplug.
That’s not just a passive bad choice in advertisers, that’s a “let’s make space to put this fake link in.”
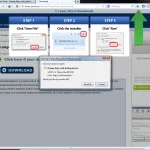
Above: Dell Sonicwall blocking the linked “downloader”
Developers who are looking for a free hosting platform end up directing their users to a data mining software that requires Malwarebytes to completely remove. Users install it because the page tells them to download a downloader, and they’ve been referred by a developer they trusted.
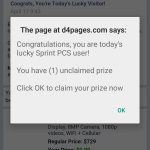
If you’re on a phone you simply get redirected to a phishing site that says you’re a winner, need to register, yadda yadda yadda.
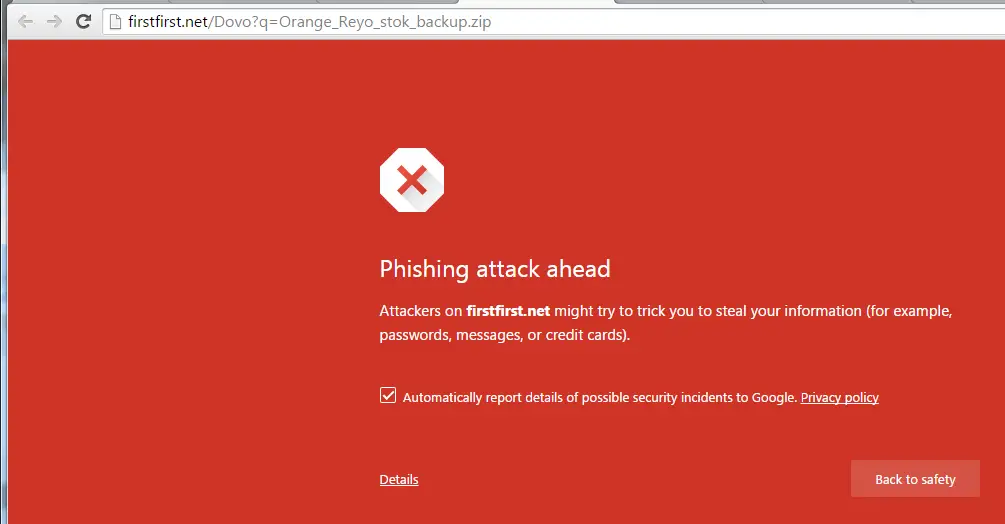
Above: Chrome doesn’t like their link
While Chrome will fire warnings at you that the site is a phishing attack, it didn’t appear that Internet Explorer’s phishing detection, or anything in a stock Firefox install gave any sort of warning before downloading. I don’t know whether post-download file scan would reveal anything as my corporate firewall blocks the files from downloading as even it knows they’re malware, or at least unwanted, and at the moment I’m not about to set up a virtual machine to test what damage the payload does.
Below: several pictures from Chrome Beta on Android over Sprint, Chrome on Windows over Comcast, Firefox on Windows over TOR, Internet Explorer over TW-Telecom/Level3.
Here’s a little excerpt from the script that’s on the download page – keep in mind this is code hosted by Dev-Host, this is not in an advertising frame, Javascript popout, etc. Unless they’re doing something extremely odd, this is all code they control:
$(‘#downloadfile2’).on(‘click’, function() {
console.log(‘.’);
//_gaq.push([‘_trackEvent’, ‘ADS’, ‘Fake Download‘, ‘6OF’]);
ga(‘send’, ‘event’, ‘ADS’, ‘Fake Download‘, ‘6OF’);});
});try{
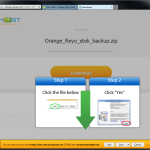
document.write(‘<a id=”downloadfile2″ href=”http://’ + lp_0 + ‘?q=Orange_Reyo_stok_backup.zip’ + ‘” target=”_blank”><div class=”button-text”>Download</div></a><br />’);
} catch(e) {
document.write(“<a id=’downloadfile2′ href=’http://firstfirst.net/Dovo?q=” + “Orange_Reyo_stok_backup.zip” + “‘ target=’_blank’><div class=’button-text’>Download</div></a><br />”);
}
The important part of this is the the very clearly labeled “Fake Download” part. The rest of the script is just it popping the button and sending them to firstfirst.net with a URL that contains the name of the file you wanted to download. I’ll point out that the “Orange_Reyo_stok_backup.zip” has nothing to do with this, it’s just the first thing that pops up on the search function. Doesn’t matter what file you attempt, the results are the same.
If it hadn’t been labeled “fake download” there’s a good chance I would have given them the benefit of the doubt.
Here’s the source code to the page as served up in Chrome – just in case you want to see the page source before it gets modified.
Anyway, that’s about it. If you’ve got a developer you trust using Dev-Host, might want to tell them to use something else as their good name is going to be associated with adware/malware distribution very quickly.
I realize most people are familiar with malware enough to recognize something is fishy, but people already have problems trusting developers with the products they trust their devices to, why add to the unease with a malware distribution center. This makes the ROM and development communities look bad.
While Dev-Host seemed to have started with the best of intentions, their money model appears now to be to prey on the trust in developers that unsuspecting end users have, and to hope they trust that developer enough to click the run button for the fake downloader.
And that’s not good.
With unlimited bandwidth hosting packages coming so cheaply these days (here’s an example, I’m not claiming they’re great), and how simple it is to distribute product via torrent without the need for paid hosting, there’s no call for this kind of shenanigans.
Force the user to watch an ad if you have to make some money, make them use a plugin torrent downloader if you can’t pay for bandwidth, but please don’t base your business on trying to trick your users into installing garbage that’s riddled with security holes as it’s written by the lowest bidder.