Flaw in Android MMS allows attacker full access
 It’s been a bad couple of months in text messaging flaws, starting with Apple and the kill text, and now the announcement of an Android MMS exploit that gives full access to an attacker – that Google became aware of in April.
It’s been a bad couple of months in text messaging flaws, starting with Apple and the kill text, and now the announcement of an Android MMS exploit that gives full access to an attacker – that Google became aware of in April.
The exploit comes as an MMS video. If you use Hangouts you’ll be exploited immediately, and if you use the default messaging client you’ll be attacked when you check the message.
They’re pretty vague on the exact steps required to make this happen, but it’s probably a bounding error that causes some Android code embedded in the MMS “video” they sent to execute.
Google has already provided all partners with patches, but as most of you are aware, the people who manufacture your phone, or the carriers that it’s on, are money grubbing asshats who will let you get infected if it means more phone sales or profits. Google only expects 20-50% of Android devices to be patched due to the open ecosystem and asshats.
Fortunately, and I don’t know why nobody seems to be reporting this, a fix doesn’t have to be done on the Android device, which is what most places seem to be missing. Your Android device doesn’t process MMSs end to end – an MMS server run by your carrier does.
They already block spam, robotexting, images of The Goat, etc. Seems like putting a new rule in to check for a very specifically crafted malformed MMS would be child’s play for the carrier messaging commandos, rendering this a nearly complete non-issue for the end users.
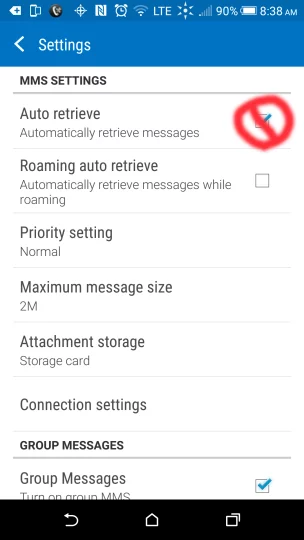
In the meantime, should you worry about this, yet another thing that’s not being reported is that you can simply disable MMS auto retrieval on 100% of the phones that are affected, and choose to only download MMSs from people you know. While they still could be infected and sending you the payload, chances are you’ll have a clue.
If you’re unable in Hangouts to choose to disable auto-retrieve, simply open up the Android messaging client and disable it there. You’ll be prompted on any incoming SMSs whether you want to download them or not. Just don’t accept SMS from people you don’t know and you should be fine.
And rather than waiting for your carrier to get a patch from your phone manufacturer and push it to you, shoot them a nice email explaining that you would like them to check for and block at the server level Android MMS exploits.
[NPR]

