Several remote assistance apps on Android vulnerable to exploit
 In yet another vulnerability news, OEM preinstalled TeamViewer, CommuniTake Remote Care, and MobileSupport by Rsupport remote assistance apps (among others) are vulnerable to the same exploit giving hackers complete control of your device.
In yet another vulnerability news, OEM preinstalled TeamViewer, CommuniTake Remote Care, and MobileSupport by Rsupport remote assistance apps (among others) are vulnerable to the same exploit giving hackers complete control of your device.
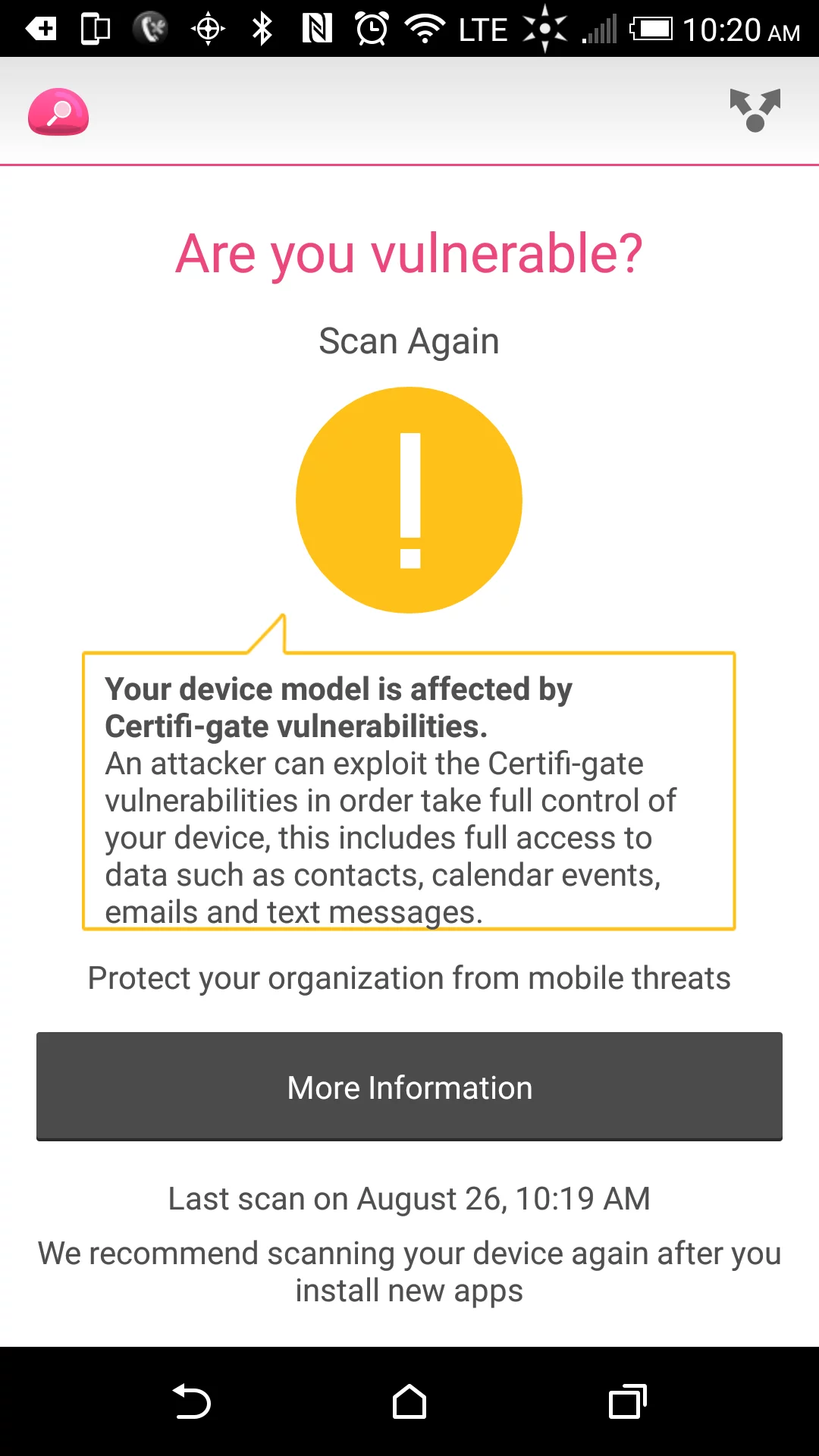
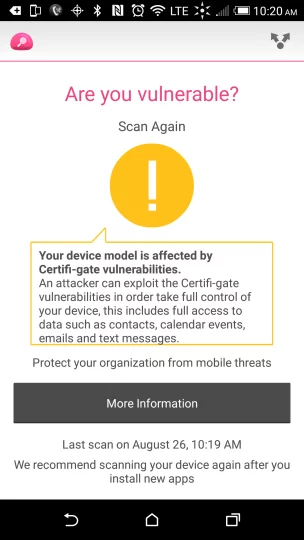
This latest round of exploits has been dubbed Certifi-gate after how the exploitable modules were signed by the manufacturers which tells Android to trust them.
These apps are commonly pre-installed on Samsung, LG, and HTC devices. It’s unclear why all of these are exploitable via similar methods unless they just got lazy and purchased the same code and branded it as theirs.
When your Apple and Windows Phone friends start poking fun of Android security, it should be noted this is not an Android bug, but something stupid that the manufacturers put into their custom version of Android they shipped with the phone.
One app in the Play Store was found to be actively exploiting the vulnerability called “EASY screen recorder,” and was removed. It doesn’t appear as though the app was malicious, it was just using the exploit to grab the screen like it said it could do. So there’s that.
The exploitable plugin is trusted as a system service, is signed by the manufacturers, so it can do pretty much anything the system user can do.
Affected users can scan their devices for the vulnerability using a free vulnerability scanner from Check Point Software. Yes, the stock HTC One M9 is affected.
What can you do?
It appears that the vulnerability can only be exploited by code running on your phone. Google is now scanning for attempts to access it, so as long as they’re doing their job you should be able to rest easier until the manufacturers get off their keisters.
Other markets than Google Play remain questionable for their scanning abilities, and anything you download from ThePirateBay claiming to be some amazeballs free app is highly suspect.
You can also root your phone, remove the exploitable modules, then unroot your phone, which is generally much more difficult than it sounds because the manufacturers, in the name of security, which evidently they don’t properly understand, have put up a lot of roadblocks to rooting.
Other than that, wait for the device manufacturers to push a fix to the carriers (this is manufacturer garbage, not Android garbage), the carriers to certify it, then to push it, by which time the exploit will be old enough to vote.
[ars technica]